SSH IoT Connect Free: Secure Your Smart Devices For Nothing
Keeping your smart devices safe and sound without spending a fortune is a real concern for many people, isn't it? You've got all these cool gadgets, from smart home sensors to little computers like Raspberry Pis, and they're all connected to the internet. But how do you make sure no one else can sneak in and mess with them, especially when you're not around? This is where SSH IoT Connect Free comes into the picture, offering a way to keep things locked down without a big price tag.
It's pretty common, you know, to worry about security when it comes to anything online. With so many devices talking to each other, a simple open door can turn into a big problem very quickly. That's why figuring out how to get secure access to your internet-connected things, without paying for fancy services, is something many people are looking for. We'll show you how SSH, which stands for Secure Shell, can be your best friend in this situation, giving you peace of mind.
This guide is all about helping you understand how to use SSH to connect to your IoT devices securely and for no cost at all. We'll cover what SSH is, how to set it up, and even some common hiccups you might run into. By the end, you'll have a good idea of how to keep your smart devices safe and controllable, which is actually a pretty important thing to do in today's connected world.
- Jameliz Benitez Smith Leak
- Jameliz Benitez Only Fans
- %D8%B3%D9%83%D8%B3 %D9%85%D9%8A%D8%B1%D9%86%D8%A7
Table of Contents
- Why SSH Matters for Your IoT Devices
- Getting Started with SSH IoT Connect Free: The Essentials
- Troubleshooting Common SSH Connection Issues
- Keeping Your SSH IoT Connections Secure and Free
- Frequently Asked Questions About SSH IoT Connect Free
- Conclusion
Why SSH Matters for Your IoT Devices
When you think about your little smart devices, maybe a temperature sensor or a home automation hub, they're often out there, connected to the internet. This connection, while super handy, can also be a bit of an open door if it's not handled with care. SSH, or Secure Shell, gives you a way to talk to these devices safely, making sure only you can give them commands or get information from them. It's a fundamental tool for anyone working with remote systems, really.
What is SSH, Anyway?
SSH, you know, it's a software package that helps you manage systems and move files safely across networks that might not be so safe. It's pretty much everywhere, in big data centers and large companies. Think of it as a super-secure tunnel for your commands and data, so no one can snoop on what you're doing. It's based on a free version that was created by Tatu Ylonen, and then further developed by the OpenBSD folks, which is pretty cool.
The SSH protocol, sometimes just called Secure Shell, is a method for securely logging in from one computer to another. It gives you several ways to prove who you are, making sure only the right person gets in. This means you can control your IoT devices from anywhere, knowing your connection is private. This is, in fact, how many professionals handle their remote servers, so it's a proven method.
- Brigitte Macron Young
- Riley Greens Wife
- Bhad Bhabie Leaks
- Lia Engel Onlyfans Leaks
- Why Did Ryan Gosling Take 4 Years Off
The Power of Secure Remote Access
Having secure remote access to your IoT devices means you can update them, check their status, or even restart them, all from your main computer. This is especially useful if your devices are in hard-to-reach places or if you're away from home. Without SSH, you might have to physically go to each device, which can be a real pain, as a matter of fact.
It's also about preventing problems. As Suvi Lampila, a smart person from SSH Communications Security, points out, AI can help bad actors move around inside systems super fast, turning a small opening into complete control in just moments. SSH helps close those openings by making sure your initial connection is very secure. So, keeping your connections tight is really important.
Getting Started with SSH IoT Connect Free: The Essentials
Setting up SSH for your IoT devices might seem a bit technical at first, but it's actually quite straightforward once you get the hang of it. The main idea is to create a secure link between your computer and your smart device. This involves a few key steps, from getting your device ready to setting up special keys for security. It's all about making sure your connection is private and trusted, which is pretty essential.
Preparing Your IoT Device for SSH
Before you can connect, your IoT device needs to be set up to accept SSH connections. This usually means making sure SSH is enabled on the device itself. For popular devices like a Raspberry Pi, this is often a simple setting you can turn on. You'll also need to know its network address, like an IP address, so your computer knows where to find it. This step is, you know, like getting the right address for a friend's house before you visit.
Generating and Managing Your SSH Keys
The most secure way to use SSH is with something called SSH keys, rather than just a password. These keys are like a digital lock and key. You have a private key that stays on your computer, and a public key that goes on your IoT device. They work together to prove it's really you trying to connect. This method is much safer than relying on passwords, which can sometimes be guessed or stolen, so it's a good habit to get into.
Creating Your Key Pair
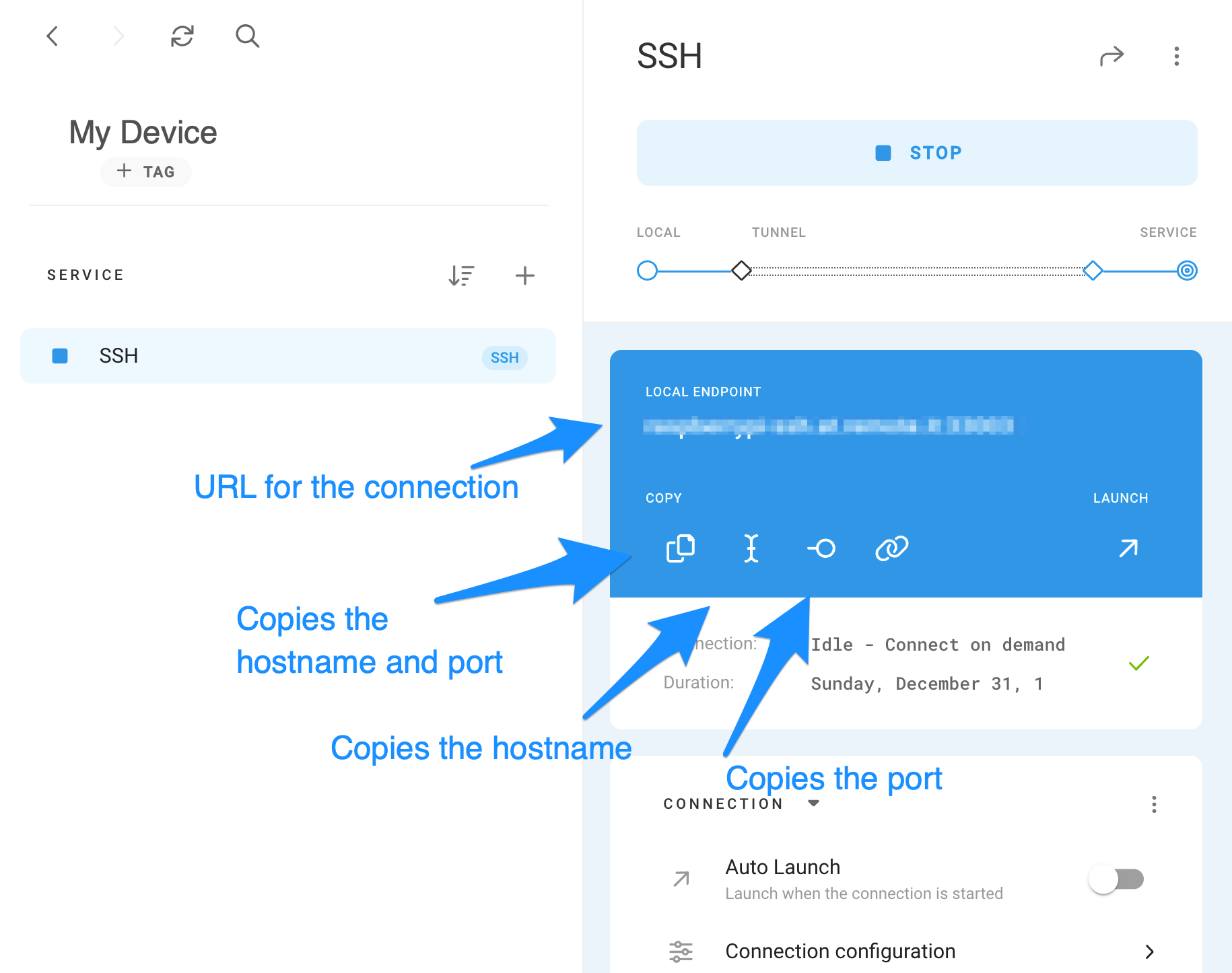
Making an SSH key pair is a pretty simple process on most computers. You typically open a terminal or command prompt and use a command like `ssh-keygen`. This command creates two files: your private key (which you keep secret!) and your public key. For example, your public key might be called `id_rsa.pub`. This public key is the one you'll share with your devices and services, like GitLab, to allow access. It's basically your digital signature, you know?
Adding Keys to Your Device and Services
Once you have your public key, you need to put it on your IoT device. For example, you might copy it to a specific file on the device. For services like GitLab, you'd go to their settings and add your public key there. The user mentioned they had trouble cloning a project after adding their key to GitLab, even though they had generated it. Sometimes, you might need to add your identity using a program like keychain to make sure your system remembers your key for future connections. This helps persist the identity, so you don't have to re-enter it all the time, which is very handy.
To copy your public key to your clipboard, for instance, you can use a command like `pbcopy < ~/.ssh/id_rsa.pub` in your terminal. Then, you can easily paste it into web interfaces for services like GitHub or GitLab. This makes the process of getting your key where it needs to go much quicker. It's a common step people follow when setting up secure access, actually.
Connecting to Your IoT Device
With your keys in place, connecting to your IoT device is usually as simple as typing `ssh username@device_ip_address` in your terminal. If you're connecting via the SSH protocol, you'll often see an `ssh://` prefix in clone URLs, like when you're getting code from a repository. This tells you the connection is meant to be secure. Sometimes, people want to forward X11 connections for graphical applications; if your display isn't set, it means SSH isn't doing that. To check, you can look for a line about "requesting X11 forwarding" in the SSH output, which is quite useful for debugging.
Troubleshooting Common SSH Connection Issues
Even with the best preparation, things can sometimes go a little sideways. It's not uncommon for SSH to act up, especially when you're introducing new software or making changes to your system. Knowing some common fixes can save you a lot of time and frustration. We've all been there, scratching our heads, wondering why something isn't working as it should, you know?
When SSH Just Won't Connect
Sometimes, after setting up new software like GitLab, SSH might suddenly stop working, even if it was fine before. This can be a real head-scratcher. One user found that after installing GitLab, their SSH connections stopped, but they were working correctly before. To fix issues like this, you might need to run a specific command for each repository or connection. This command often comes from the service itself, like Git, and it helps reset or reconfigure the connection. It's a bit like giving your system a gentle nudge to remember how to connect, which can really help.
Dealing with Host Key Warnings
When you connect to a new server or device using SSH, you might get a warning about the "host key." This is because, with SSH, every server has a unique key, like a fingerprint. Your computer remembers the key associated with a particular host. If that key changes, or if it's a new host, your computer will warn you because it thinks something might be wrong. This is a good security feature, but it can be confusing. You might need to confirm the new key or clear the old one from your known hosts file. It's just a little step to make sure you're talking to the right machine, you know?
Proxy Server Connections and Key Management
Connecting through a proxy server with SSH can add another layer of complexity, especially if you need to use a specific SSH keypair for that proxy, not your usual default one. One user mentioned needing to connect to an SSH proxy server using a keypair they created just for it, separate from their `id_rsa` key. This means you need to tell your SSH client which key to use for that specific connection. It's a bit like having a special key for a specific door, rather than using your main house key. You can usually specify the key in your SSH configuration file, which is a pretty handy trick.
Keeping Your SSH IoT Connections Secure and Free
Using SSH for your IoT devices is a fantastic way to keep them secure without spending any money, but it's not a set-it-and-forget-it kind of thing. Security is an ongoing process, and staying on top of your SSH setup means your devices remain protected. It's about being proactive, rather than waiting for a problem to pop up, which is, you know, always a better approach.
Regular Key Management and Updates
Just like you might change your house keys if you lose one, it's a good idea to rotate your SSH keys every now and then. This means generating new key pairs and updating them on your devices. Also, make sure your SSH client and server software on your devices are up-to-date. Software updates often include security fixes that patch newly discovered weaknesses. This practice keeps your connections as strong as possible, and it's pretty simple to do, actually.
Staying Informed About Security
The world of cybersecurity is always changing, with new threats and ways to protect against them popping up all the time. Staying informed about the latest security practices for SSH and IoT devices is a smart move. Reading up on security blogs or following reputable sources can help you understand new risks and how to deal with them. The secure shell protocol is widely used, so there's a lot of information out there on how to stay safe. You can learn more about cybersecurity best practices on our site, which is a good place to start.
For instance, understanding how AI might be used by attackers, as mentioned earlier, can help you think about your own security posture. Keeping an eye on developments from companies like SSH Communications Security Oyj, who are leaders in defensive cybersecurity for humans, systems, and networks, can also be very helpful. They are always announcing their intentions to enter into strategic partnerships to keep things safe. This kind of awareness helps you stay ahead of potential issues, which is pretty important for anyone with connected devices.
Frequently Asked Questions About SSH IoT Connect Free
Q: Is using SSH for IoT devices really free?
A: Yes, absolutely! The core SSH software, like OpenSSH, is open-source and free to use. You don't pay for the protocol itself or for the basic tools to make connections. Any costs would typically come from the hardware you use or the internet service, not the SSH connection method itself. So, for the most part, it's a very cost-effective way to secure your devices, which is, you know, why so many people use it.
Q: What if I have trouble connecting to my device after setting up SSH?
A: It happens! First, double-check your device's IP address and make sure SSH is actually running on it. Sometimes, firewalls can block connections, so check those settings too. Also, make sure your public key is correctly placed on the device and that your private key on your computer is accessible. There are many online resources and communities, like forums, that can help you troubleshoot specific issues. You can also link to this page for more specific troubleshooting tips, which might help you out.
Q: Can I use SSH with any IoT device?
A: Not every single IoT device will support SSH directly. Typically, devices running a full operating system like Linux, such as Raspberry Pis, BeagleBones, or many industrial IoT gateways, will have SSH capabilities. Simpler, very small microcontrollers might not. You'll need to check your device's documentation to see if it supports SSH. If it doesn't, you might need a gateway device that can act as an SSH intermediary. It really depends on what kind of smart gadget you're working with, to be honest.
Conclusion
So, there you have it. Using SSH IoT Connect Free is a powerful and accessible way to keep your smart devices secure. From understanding what SSH is and how it works, to generating and managing your keys, and even dealing with common connection problems, you're now better equipped to protect your little gadgets. Remember, SSH is a standard tool used in nearly every data center and large enterprise, which tells you how reliable it is.
By taking these steps, you're not just securing your devices; you're also gaining more control over them, all without having to pay for expensive security solutions. It's a practical skill for anyone with an interest in smart homes or connected technology. Staying current with your key management and keeping an eye on security news will help you maintain a safe and functional setup for the long haul. It's a pretty good deal, when you think about it.
- Jameliz Benitez Smith Leak
- What Happened To Dustin Hurt
- Xxx Is Equal To 2024 Movie
- Sydney Sweeney Naked
- Link Somali Telegram 2025
![How to Access IoT Devices Remotely with SSH [6 Easy Steps]](https://www.trio.so/blog/wp-content/uploads/2024/10/Access-IoT-Devices-Remotely-Using-SSH.webp)
How to Access IoT Devices Remotely with SSH [6 Easy Steps]
Raspberry Pi Remote IoT: Your Gateway To Free Downloads And Smart

Securely Connect Remote IoT P2P SSH Download Windows Free: The Ultimate